Data Connectors provide
- Secure and private data collection and processing within Trusted Execution Environments (TEEs).
- Verifiable proofs of secure data handling and processing.
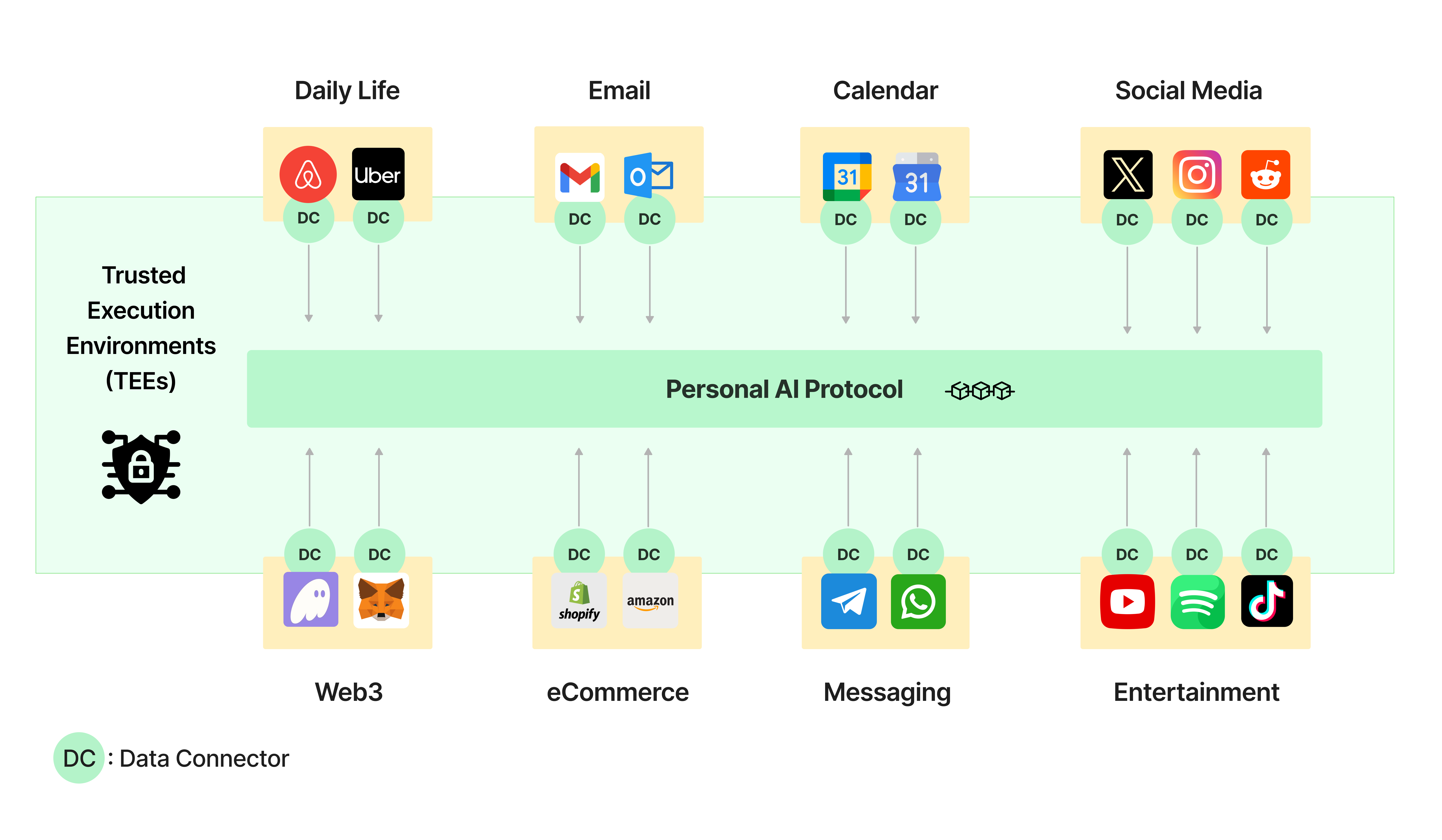
How do they work?
PIN AI app users choose the data they want Data Connectors to gather and securely store in their trusted location. The process consists of the following steps:Data collection
The connector establishes a secure connection to the data source. The user grants permission for the connector to access their data.
- Once authorized, the connector uses API calls (requests) with the appropriate API key or access token to fetch the specific data the user has authorized it to access.
Processing
Connectors clean, format, and structure retrieved data into a personal index, a specialized optimized for Personal AI.
Onchain verification
Connectors submit hardware-generated attestation reports to the PIN Network, providing verifiable proof of secure data handling and processing within TEE nodes. These reports confirm that:
- The TEE node has completed the assigned task.
- The code running inside the TEE is the version certified by the Personal AI Protocol, ensuring no alterations to the software or environment.
Storage
After verification, processed data is securely stored in the user’s chosen trusted location—for example, their local device, a personal cloud storage account, or a dedicated secure storage solution. This gives users control over their data, ensuring privacy and direct access for their Personal AI.
Key features
- Privacy-preserving data handling: All data fetching and processing occur exclusively within a TEE node, unless otherwise authorized by the user. This prevents unauthorized access or data leakage.
- User-controlled access: Users retain full control over which Data Connectors can access their apps and under what conditions. Data fetching is customizable based on user-defined parameters, such as scheduled updates or on-demand fetching.